Data Brokers and Targeted Advertising How Your Online Behavior is Trac…
페이지 정보

본문
In the digital age, the seamless integration of technology into our daily lives has brought about a profound transformation in how we interact with the world. This section delves into the mechanisms that underpin the collection and utilization of user data, shedding light on the complex interplay between technology and personal autonomy. It explores the ethical implications and the broader societal effects of these practices, which are often hidden from public view.
Unveiling the Practices of Information Aggregators: At the heart of this discussion lies the role of entities that specialize in the collation of user data. These organizations operate in a realm where the boundaries of privacy and consent are frequently blurred. By examining their methodologies, we can better understand the extent to which individual behaviors are monitored and analyzed.
The Influence of Personal Data on Marketing Strategies: One of the primary applications of aggregated user information is in the realm of marketing. Companies leverage this data to tailor their promotional efforts, aiming to enhance the relevance of their messages to specific demographics. This practice raises significant questions about the balance between commercial interests and the rights of individuals to maintain control over their personal details.
Navigating the challenges posed by these developments requires a nuanced understanding of both the technological capabilities and the ethical frameworks that govern them. As we continue to explore this topic, it becomes evident that the conversation around digital surveillance and its impact on personal autonomy is far from over.
Understanding Data Brokers
This section delves into the intricate operations of entities that specialize in the collection and distribution of user details. These organizations play a pivotal role in the modern digital landscape, influencing various aspects of online interactions and marketing strategies.
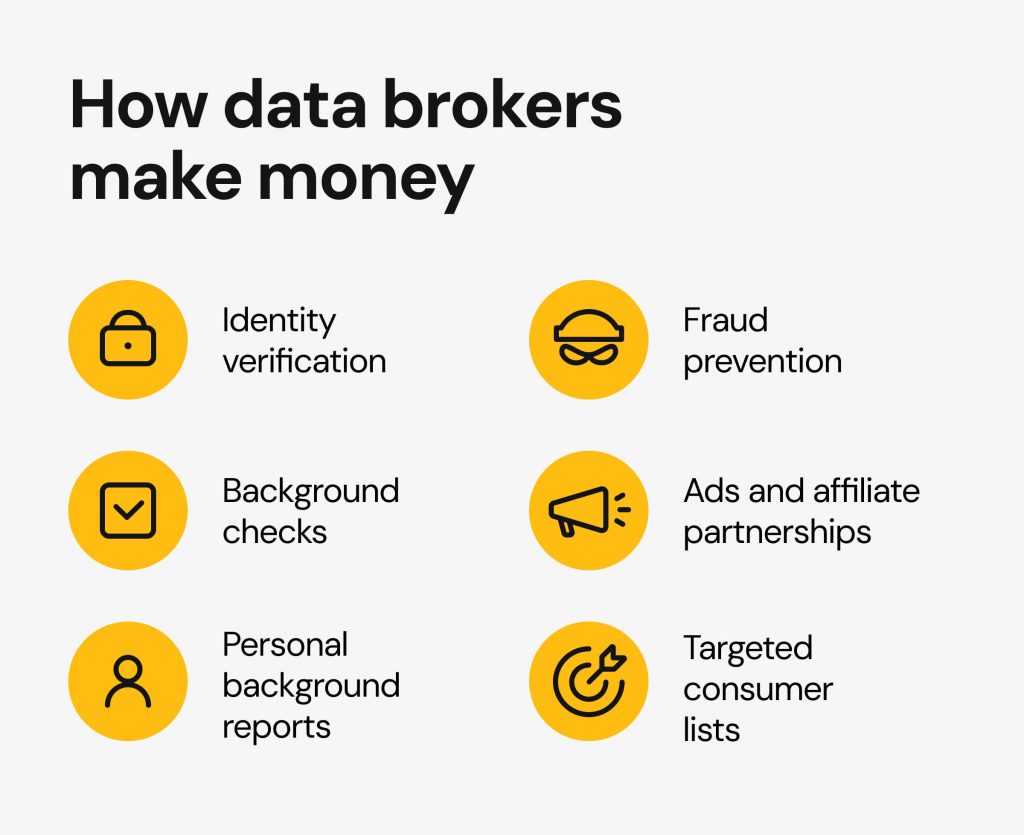
Data brokers, often operating behind the scenes, are entities that gather and sell user data. This data is typically used for enhancing marketing efforts, enabling businesses to tailor their advertisements more precisely to individual preferences and behaviors. The functionality of these brokers can be broken down into several key components:
| Function | Description |
|---|---|
| Data Collection | Data brokers collect information from a variety of sources, including public records, social media, and online browsing habits. |
| Data Aggregation | Once collected, the data is aggregated and organized into comprehensive profiles that can include demographic, behavioral, and financial information. |
| Data Analysis | The aggregated data is analyzed to identify patterns and trends, which can be used to predict consumer behavior and preferences. |
| Data Distribution | The analyzed data is then sold to various entities, including marketers, retailers, and financial institutions, who use it to refine their marketing strategies and customer targeting. |
Understanding the role and functionality of data brokers is crucial for comprehending the mechanisms behind modern marketing and the implications for individual privacy. As these brokers continue to evolve, it becomes increasingly important to consider the ethical and legal dimensions of their operations.
Role and Functionality of Data Brokers
This section delves into the mechanisms through which entities gather and utilize individual details for various purposes. Understanding these processes is crucial for comprehending the broader implications of data management in today's digital landscape.
Data aggregators, often operating behind the scenes, collect a vast array of user details from numerous sources. These can include public records, social media profiles, and even purchase histories. The information is then compiled and analyzed to create comprehensive profiles of individuals, which are used to tailor services and products to specific consumer segments.
One of the primary sources of data for these aggregators is online activity. Every click, search, and interaction on the internet can be monitored and recorded. This data is then aggregated with other information to build a detailed picture of a user's interests, behaviors, and preferences.
Another significant source of data is transactional records. This includes details from credit card purchases, online shopping, and even subscription services. By analyzing these transactions, data aggregators can infer a wealth of information about an individual's lifestyle, spending habits, and financial status.
Public records also play a crucial role in data collection. Information such as property records, marriage licenses, and court documents are all accessible sources of data. These records can provide insights into an individual's personal life, financial situation, and legal history.
Lastly, surveys and feedback forms are another avenue through which data is collected. Often, users willingly provide personal details in exchange for services or to participate in market research. This data is valuable as it is directly provided by the individuals and can be used to verify or supplement other collected information.
In summary, the role of data aggregators is multifaceted, involving the collection of data from a variety of sources. This data is then processed and used to inform marketing strategies, product development, and other business decisions, highlighting the integral role these entities play in the modern digital economy.
Sources of Personal Information
This section delves into the various channels through which individual details are collected and utilized. It explores the mechanisms by which entities gather data, shedding light on the breadth and depth of information acquisition in today's digital landscape.
Digital Footprints: Every interaction on the internet leaves a trace. From browsing history to search queries, these digital footprints are meticulously recorded. Social media platforms, e-commerce websites, and online forums are prime sources where user activities are logged and analyzed.
Public Records: Government databases, property records, and court documents are accessible sources of personal data. These records, although public, can be aggregated and analyzed to build comprehensive profiles of individuals.
Surveys and Forms: Online and offline surveys, registration forms, and feedback submissions are common methods for collecting personal details. Often, these are used for market research or to enhance user experience, but they also serve as rich sources of personal information.
Transactional Data: Every financial transaction, whether through credit cards, online payment platforms, or direct bank transfers, generates data. This transactional information can reveal spending habits, financial status, and more.
Cookies and Tracking Technologies: Websites use cookies and similar technologies to track user activities. These tools help in understanding user preferences and behaviors, which can be valuable for tailoring content and services.
Understanding these sources is crucial as it helps in recognizing the extent to which personal data is collected and used, thereby empowering individuals to make informed decisions about their digital interactions.
Impact of Targeted Advertising
![]()
This section delves into the profound effects that tailored promotional strategies have on consumer interactions and market dynamics. By examining the mechanisms through which these strategies are implemented, we gain insights into their broader implications on consumer choices and market efficiency.
Tailored promotional strategies utilize various methods to gather and analyze consumer data, enabling advertisers to present products or services that closely match individual preferences and past purchasing behaviors. This approach not only enhances the relevance of advertisements but also potentially influences consumer decision-making processes.
| Method | Description | Impact |
|---|---|---|
| Cookies | Small text files stored on a user's device that record browsing history and preferences. | Enables personalized ads based on browsing activity, enhancing ad relevance. |
| Pixel Tags | Tiny, invisible graphics that track user interactions with web pages. | Helps in measuring the effectiveness of advertising campaigns and refining targeting strategies. |
| Social Media Analytics | Analysis of user data from social platforms to understand behavior and preferences. | Facilitates the delivery of highly targeted ads on social media platforms, increasing engagement. |
The implementation of these methods raises significant concerns regarding user privacy and the ethical use of collected data. As such, it is crucial to consider the regulatory frameworks and ethical guidelines that govern the use of such technologies in advertising.
In conclusion, while tailored promotional strategies can significantly enhance the efficiency of marketing efforts, their deployment must be balanced with considerations for consumer privacy and ethical data practices. Understanding these mechanisms is essential for both consumers and businesses to navigate the evolving landscape of digital marketing effectively.
Mechanisms of Online Tracking
This section delves into the intricate methods employed by various entities to monitor and analyze user activities on the internet. These techniques are pivotal in understanding the broader implications of digital surveillance on individual behaviors and preferences.
Online tracking mechanisms primarily rely on the collection and analysis of data points that users generate as they navigate the web. These data points can range from simple browsing history to more complex behavioral patterns. Below is a table summarizing the key methods used for tracking:
| Method | Description | Impact |
|---|---|---|
| Cookies | Small text files stored on a user's device that help websites remember information about the user's visits. | Enables personalized content and ads, but can also lead to privacy concerns as they track user activity across different sites. |
| Web Beacons | Tiny, invisible images embedded in web opt out white pages or emails that are used to track user interaction. | Help in measuring the effectiveness of web pages or email campaigns, but also contribute to tracking user behavior without their knowledge. |
| Fingerprinting | Technique that gathers information about a user's device configuration to uniquely identify them. | Provides a robust method of tracking even when cookies are blocked, raising significant privacy issues. |
| Social Media Tracking | Uses social media plugins or login credentials to track user activities across the web. | Facilitates targeted marketing but also exposes extensive personal data, potentially violating user privacy. |
Each of these mechanisms plays a crucial role in shaping the digital landscape, influencing not only how information is presented to users but also how their behaviors are analyzed and predicted. Understanding these mechanisms is essential for users to make informed decisions about their online privacy and security.
Effects on Consumer Behavior
This section delves into the profound impact that sophisticated marketing techniques have on the purchasing decisions and overall behavior of consumers. By analyzing the mechanisms through which promotional strategies influence consumer choices, we aim to shed light on the broader implications of these practices.
The influence of tailored marketing extends beyond mere product selection; it shapes consumer preferences and behaviors in several significant ways:
- Increased Engagement: Consumers are more likely to interact with advertisements that closely match their interests, leading to higher engagement rates.
- Enhanced Persuasion: Tailored messages are often more persuasive, as they address specific needs or desires of the consumer, thereby increasing the likelihood of a purchase.
- Behavioral Shifts: Over time, repeated exposure to certain types of promotions can subtly shift consumer behavior, encouraging habitual purchasing of particular products or brands.
- Perception of Personalization: Consumers often perceive personalized marketing as a positive aspect of their shopping experience, which can enhance brand loyalty and satisfaction.
However, the effects of such marketing strategies are not uniformly positive. There are several potential downsides that can impact consumer behavior negatively:
- Privacy Concerns: The collection and use of personal data for marketing purposes can lead to heightened concerns about privacy, potentially eroding trust in brands and platforms.
- Over-saturation: Consumers may feel overwhelmed by the constant barrage of tailored advertisements, leading to ad fatigue and reduced effectiveness of marketing efforts.
- Manipulation Fears: There is a growing concern that sophisticated marketing techniques could be used to manipulate consumer decisions, undermining free will and autonomy in purchasing.
Understanding these dynamics is crucial for both consumers and businesses. For consumers, awareness of how their behaviors are influenced can empower more informed decision-making. For businesses, a balanced approach that respects consumer privacy while effectively engaging with their audience is essential for sustainable success.
Privacy Concerns and Legal Frameworks
This section delves into the intricate relationship between privacy apprehensions and the legal structures designed to address them. It explores the current legislative landscape, highlighting its strengths and identifying areas where it falls short in fully protecting individual rights in the digital age.
In the realm of digital surveillance and data collection, numerous laws have been enacted to safeguard user confidentiality. However, these regulations often face challenges in keeping pace with rapidly evolving technologies and business practices. For instance, while some statutes provide robust protection against unauthorized data access, they may lack provisions for handling new forms of data aggregation and analysis techniques.
One of the significant limitations of current privacy laws is their fragmented nature. Different jurisdictions have varying standards and enforcement mechanisms, leading to a patchwork of protections that can be difficult for both consumers and businesses to navigate. This fragmentation not only complicates compliance but also creates loopholes that can be exploited by entities seeking to bypass regulations.
Moreover, the enforcement of these laws is often hampered by limited resources and jurisdictional boundaries. Regulatory bodies may lack the necessary funding or authority to effectively monitor and penalize violations on a global scale. This can result in a lack of deterrence, encouraging non-compliance by those who calculate the risks of being caught as minimal.
Another critical limitation is the focus on reactive rather than proactive measures. Many laws are structured to address privacy breaches after they occur, rather than preventing them through proactive oversight and control mechanisms. This reactive approach leaves individuals vulnerable to privacy invasions that could have been mitigated with more proactive legal frameworks.
In conclusion, while current privacy laws have made significant strides in protecting individual data rights, they are not without their shortcomings. The rapid evolution of digital technologies necessitates a continuous review and enhancement of these legal frameworks to ensure they remain effective in the face of new challenges. This section underscores the need for a more unified, proactive, and robust legal approach to privacy protection in the digital era.
Current Privacy Laws and Their Limitations
This section delves into the existing legal frameworks designed to safeguard individual confidentiality and the digital footprint. Despite their intentions, these regulations often face significant constraints that hinder their effectiveness in fully protecting user data.
Globally, various laws have been enacted to address the growing concerns over data protection. However, these laws often suffer from several limitations:
- Scope: Many laws are limited in scope, often focusing on specific types of data or industries, leaving gaps in protection for other forms of sensitive information.
- Enforcement: Enforcement of these laws can be challenging due to limited resources or jurisdictional issues, making it difficult to hold violators accountable.
- Technological Adaptability: The rapid evolution of technology often outpaces the ability of laws to adapt, resulting in outdated regulations that fail to address current digital practices.
- International Coordination: Differences in national laws can complicate international data transfers, creating legal hurdles and potential vulnerabilities in data protection.
These limitations underscore the need for continuous review and updating of privacy laws to better align with the complexities of modern digital environments. Enhancing these laws requires a collaborative approach involving policymakers, technologists, and legal experts to ensure comprehensive protection of user data.
In conclusion, while current privacy laws are a step in the right direction, they must evolve to meet the challenges posed by the ever-changing digital landscape. This evolution is crucial to ensure that the rights and interests of individuals are adequately protected in the digital age.
Global Approaches to Data Protection
This section delves into the various strategies adopted worldwide to safeguard sensitive details from unauthorized access and misuse. It explores the diverse legislative and technological measures implemented by different nations to ensure the integrity and confidentiality of user data.
Each country has developed its own set of regulations and practices to address the challenges of data security. Here, we outline some of the prominent approaches:
- Legislation: Many countries have enacted comprehensive laws that mandate strict controls over the collection, storage, and dissemination of personal details. For instance, the General Data Protection Regulation (GDPR) in Europe sets stringent standards for data protection.
- Technological Solutions: Advanced encryption and anonymization techniques are widely used to protect data from breaches. These technologies help in masking sensitive information, making it unreadable without proper authorization.
- Industry Standards: Various industries have established their own protocols to ensure data safety. These standards often go beyond legal requirements, reflecting the sector's commitment to privacy and security.
- Public Awareness Campaigns: Governments and organizations frequently launch campaigns to educate the public about the importance of data protection and the steps individuals can take to safeguard their information.
- International Cooperation: Cross-border collaboration is crucial in combating global data threats. Sharing best practices and coordinating enforcement actions help in creating a more secure digital environment.
Understanding these global approaches is essential for anyone concerned about the safety of their personal details in the digital age. By examining the strategies employed by different nations, we can gain insights into effective methods of protecting sensitive data.
- 이전글Simple Steps for Creating a Weekly Meal Plan 24.07.08
- 다음글De Allround Dakdekker Voor Uw Dak 24.07.08
댓글목록
등록된 댓글이 없습니다.
